Ukraine Day 1054: LIVE UPDATES BELOW.
Yesterday’s live coverage of the Ukraine conflict can be found here.
- READ OUR SPECIAL REPORT:
An Invasion By Any Other Name: The Kremlin’s Dirty War in Ukraine
000000

Soldier at the front line. Photo by ATO
Two Ukrainian soldiers were wounded near Novotoshkovskoye today, TV 112 reported.
Col. Oleksandr Motuzyanik reported just one wounded at his briefing, TV 112 reported earlier.
He said Russian-backed fighters used 152-mm to fire on ATO positions near Troitskoye and also fired mortars on Novozvanovka. He said the militants “used banned weapons at night.”
He also said that shelling continued all along the Mariupol line from Krasnogorovka and Maryinka to the north via Troitskoye, Pavlopol and Gnutotov, toward the villages of Vodyanoye and Shirokino on the Sea of Azov shore. “Almost all the provocations were accompanied by firing from light weapons and only late at night the enemy released 5 mortars near Maryinka.”
In its report from 18:00 today on its Facebook page, the ATO reported 21 incidents of shelling by Russian-backed militants in this area, Ukrainska Pravda reported.
Earlier, they reported 32 incidents in their morning dispatch on Facebook, noting that militants fired from 120-mm artillery on Novozvanivtsi; they used grenade-launchers on Talakovka and Stanitsa Luganskaya and a sniper was active in Novotroitskoye.
The ATO also noted a BMP in Starognatovka, in addition to grenade-launcher and small arms fire on Gnutovo, Pavlopol, Shirokino, Maryinka, Krasnogorovka, Vodyanoye and Novotroitskoye.
On the Donetsk line, 152-mm artillery was used on positions near Troitskoye and 82-mm mortars were fired on Avdeyevka. Grenade-launchers and small arms were used on Luganskoye and Avdeyevka
On the Mariupol line, militants fired on Pavlopol with mortar-launchers and used grenade-launchers and small arms on Talakovka, Maryinka, Gnutovo, Vodyanoye, Pavlopol and Shirokino. Snipers were active near Shirokino and Talakovka.
On the Lugansk line, grenade-launchers were used on Stanitsa Luganskaya, Novotoshkovskoye and Novozvanovka.
According to a report from the DNR News agency of the self-proclaimed “Donetsk People’s Republic,” Irina Dikun, the head of the administration of the town of Zaytsevo, told Gorlovka’s Channel 6 that the Ukrainian army had fired on her town on Christmas eve, damaging some homes.
Christmas is celebrated on January 7 according to the Orthodox calendar.
The video with an interview with Dikun and scenes of damaged cottages has not appeared before January 6, 2017 in reverse image search.
At his daily briefing, the self-styled DNR defense minister Eduard Basurin said despite the holiday ceasefire, Ukrainian forces continued to use banned artillery, tanks and mortar launchers. He said 15 towns were attacked. Six homes were damaged in Zaytsevo, Sakhanka, Trudovskiye, Petrovsky District in Donetsk. He also noted sitings of 9 drones on the Donetsk line.
o Journalist Describes Effort by Russian State Media to Falsely Incriminate Poroshenko
Max Tucker, a Kyiv-based English-language journalist who has covered Ukraine for some years for European newspapers, shared a Soundcloud file of a reporter from state TV channel Rossiya-1 asking him if he would be willing to do an interview about recordings supposedly obtained by a Ukrainian journalist incriminating President Petro Poroshenko, to “boost the story’s credibility.”
o Ukrainian Defense Ministry Denies Report of Russian Hacking of Howitzers
Last month, Crowdstrike, a US cybersecurity company which tracked the hack of the Democratic National Committee (DNC) said the same Russian group, allegedly related to Russian military intelligence (still known as the GRU), was behind the hacking of Ukrainian artillery, causing losses of up to 80% of its D-30 Howitzers:
The report, issued by cybersecurity firm CrowdStrike, said a malware implant on Android devices was used to track the movements of Ukrainian artillery units and then target them. The hackers were able to access communications and geolocations of the devices, which meant the artillery could then be fired on and destroyed.
The report will further fuel concerns that Russia is deploying hacking and cyber-attacks as a tool of both war and foreign policy. The hack “extends Russian cyber-capabilities to the frontlines of the battlefield”, the report said.
But today, the Ukrainian Defense Ministry replied to Crowdstrike’s report, discounting the claims, saying that the information about the destruction of 80% of the Howitzers due to the hack “did not correspond to reality”, RBC reported. Losses were far less than those indicated and unrelated to hacking. A Ukrainian Armed Forces statement noted (translation by The Interpreter):
“The military units of the rocket forces and artillery of the Land Forces of the Ukrainian Army are fully battle-ready, equipped and capable of fulfilling specific assignments”.
Jeffrey Carr, a cybersecurity consultant, had also challenged the claim on a post on Medium.
He noted that the estimate of losses came from pro-Kremlin blogger Colonel Cassad.
Pavlo Narozhnyy, a technical adviser to Ukraine’s military, told Voice of American (VOA) in theory, the app could have been reverse-engineered and hacked, but he believed that would have been noticed. Narozhnyy told VOA:
“I personally know hundreds of gunmen in the war zone. None of them told me of D-30 losses caused by hacking or any other reason.”
— Catherine A. Fitzpatrick
Two reports published in the last 24 hours help cast more light on the use of reconnaissance drones by the Russian military in southeastern Ukraine.
The first, published by Ukrainian investigative bloggers InformNapalm, makes use of material obtained by the Ukrainian CyberAlliance (UCA), hacked from the computer of an intelligence officer in the Lugansk region.

Начальник разведки 2 АК под контролем UCA. Part 1: БЛА "Орлан-10" – Inform Napalm
Суть операции заключалась во внедрении специфического программного обеспечения на рабочий компьютер "Начальника разведки второго армейского корпуса народной милиции" (2 КНМ) российских оккупационных войск в Луганской области. После внедрения хактивистами был получен контроль пересылаемых данных между "начальником разведки" 2 КНМ, 12-м командованием резерва ВС РФ (г.
According to the report (available in Ukrainian, Russian and Czech), UCA hackers gained access to a work computer belonging to the “intelligence chief of the 2nd Army Corps of the Lugansk People’s Militia,” which is hereafter referred to as the 2KNM. As a result, UCA was able to monitor data passed between this “separatist” intelligence officer and the headquarters of the 12th Reserve Command of the Russian armed forces in Novocherkassk.
It was this very command office that was named by the Ukrainian military as a key component of Russia’s military operations by the Ukrainian government in September last year.
According to InformNapalm, UCA hackers were able to monitor communications between Novocherkassk and Lugansk on a nearly real-time basis.
InformNapalm has now published the first batch of information obtained by UCA, the full content of which has, the report claims, already been passed on and utilized by the Ukrainian military.
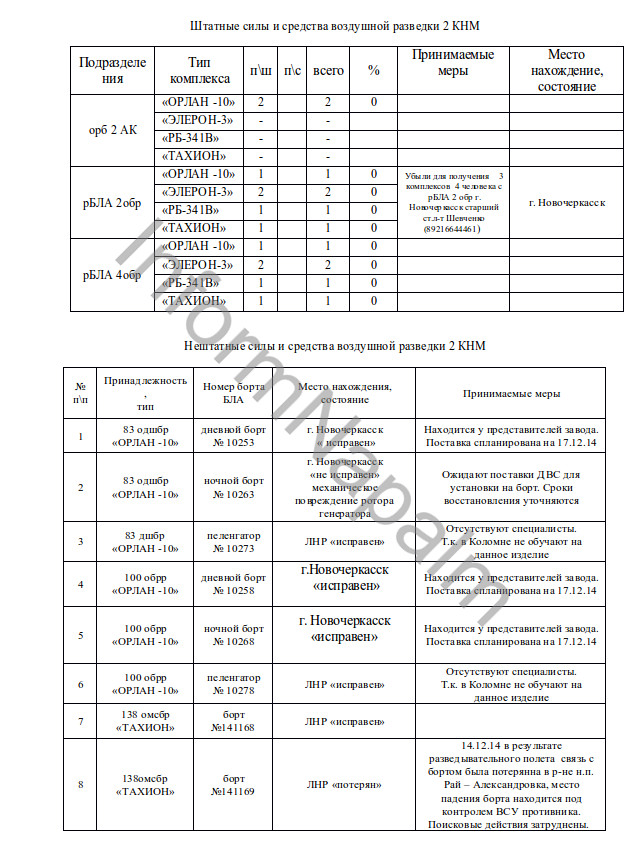
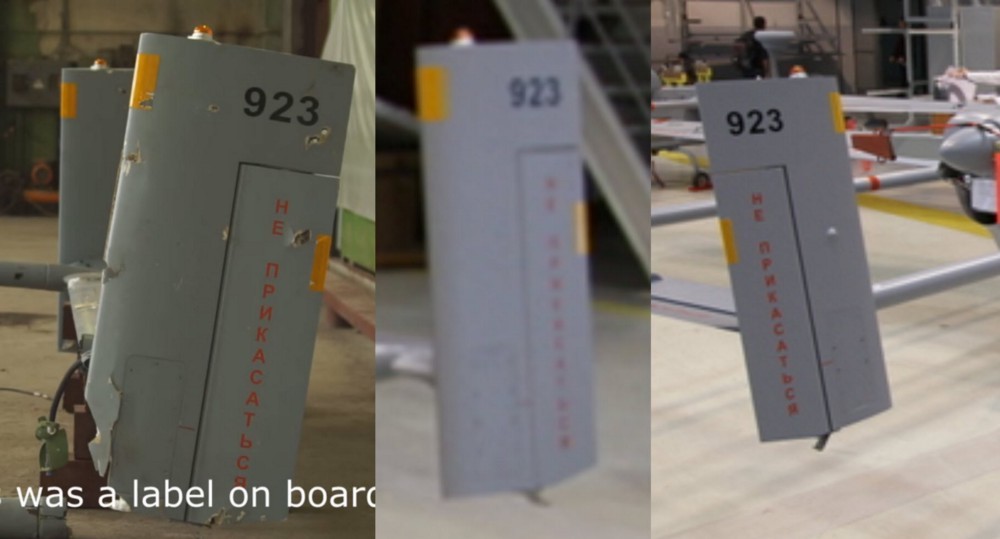
Amongst the documents included in this release are breakdowns of the reconnaissance and electronic warfare assets made available to the 2KNM by the 12th Reserve Command, some of which are labelled as having been deployed to the Lugansk region.
The list indicates the number and type of surveillance drones and the Russian army units to which they are attached, complete with individual identifying numbers.
The drone types are the Orlan-10, the Eleron-3 and the Tachyon. Several Orlan-10s have been recorded in eastern Ukraine, having crashed or been brought down by Ukrainian forces.
Also available to the 2KNM are RB-341V Leer-3 electronic warfare systems.
Ukrainian military intelligence (GUR) claimed in May 2016 that Russian Leer-3 systems were being used in concert with Orlan-10 drones to conduct reconnaissance missions near Avdeyevka, north of Donetsk.
According to the GUR, Leer-3 systems can both suppress GSM mobile communications and locate emitter locations with the aid of signals beamed from drones.
As we reported at the time, there had been several sightings in the Donetsk area that indicated the presence of at least one Leer-3:
On March 29 a short video was uploaded, purportedly showing such a system on the move in Donetsk:
According to the UCA documents, this hardware is attached to Russian army units including the 83rd Guards Air Assault Brigade, the 100th Separate Reconnaissance Brigade and the 138th Guards Motor Rifle Brigade.
The last Tachyon UAV on the list is labelled as “lost” following a loss of communications near Rai-Aleksandrovka in Ukraine.
Also released by InformNapalm was information on individual drone operators, including full names and ranks.
InformNapalm was able to confirm, using social media evidence, that some of these individuals were indeed soldiers in the Russian armed forces.
UCA hackers have also, the report claims, managed to gain access to email accounts belonging to some of the operators, finding payroll statements indicating that the men were active members of the Russian armed forces at the time that they were controlling drones flying over Ukraine.
Details on individual drone flights are amongst the data released, which, no doubt, has been of great value to Ukrainian military officers in assessing the extent to which Russian commanders are aware of their positions in the Donbass. But the most striking elements of yesterday’s release are photos and videos from drone operators’ computers.
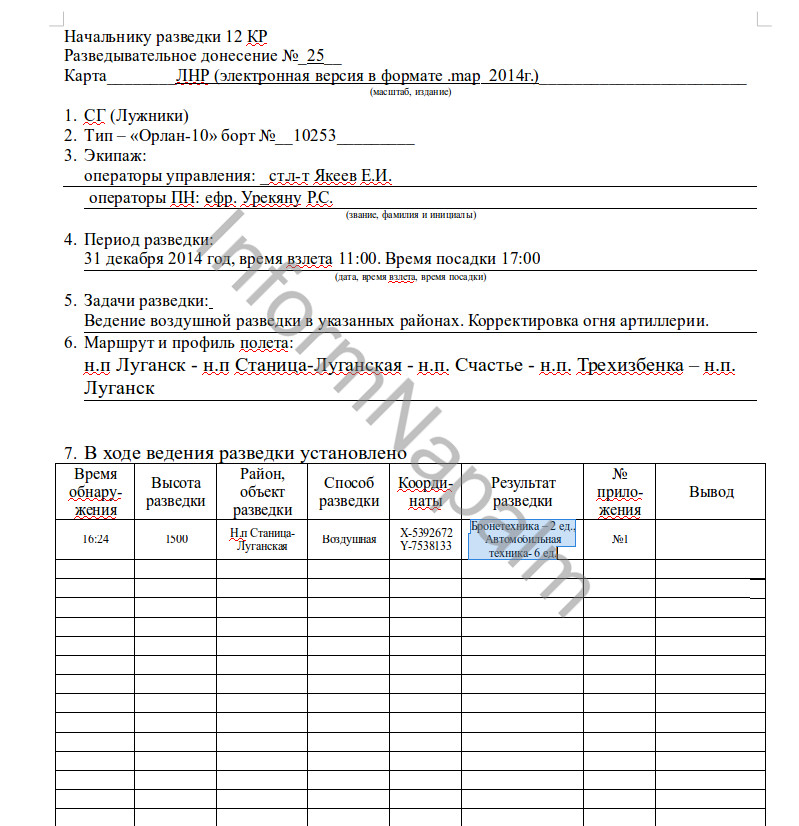
This image, from December 31, 2014, was recorded during a drone flight near Ukrainian-controlled Stanitsa Luganskaya.
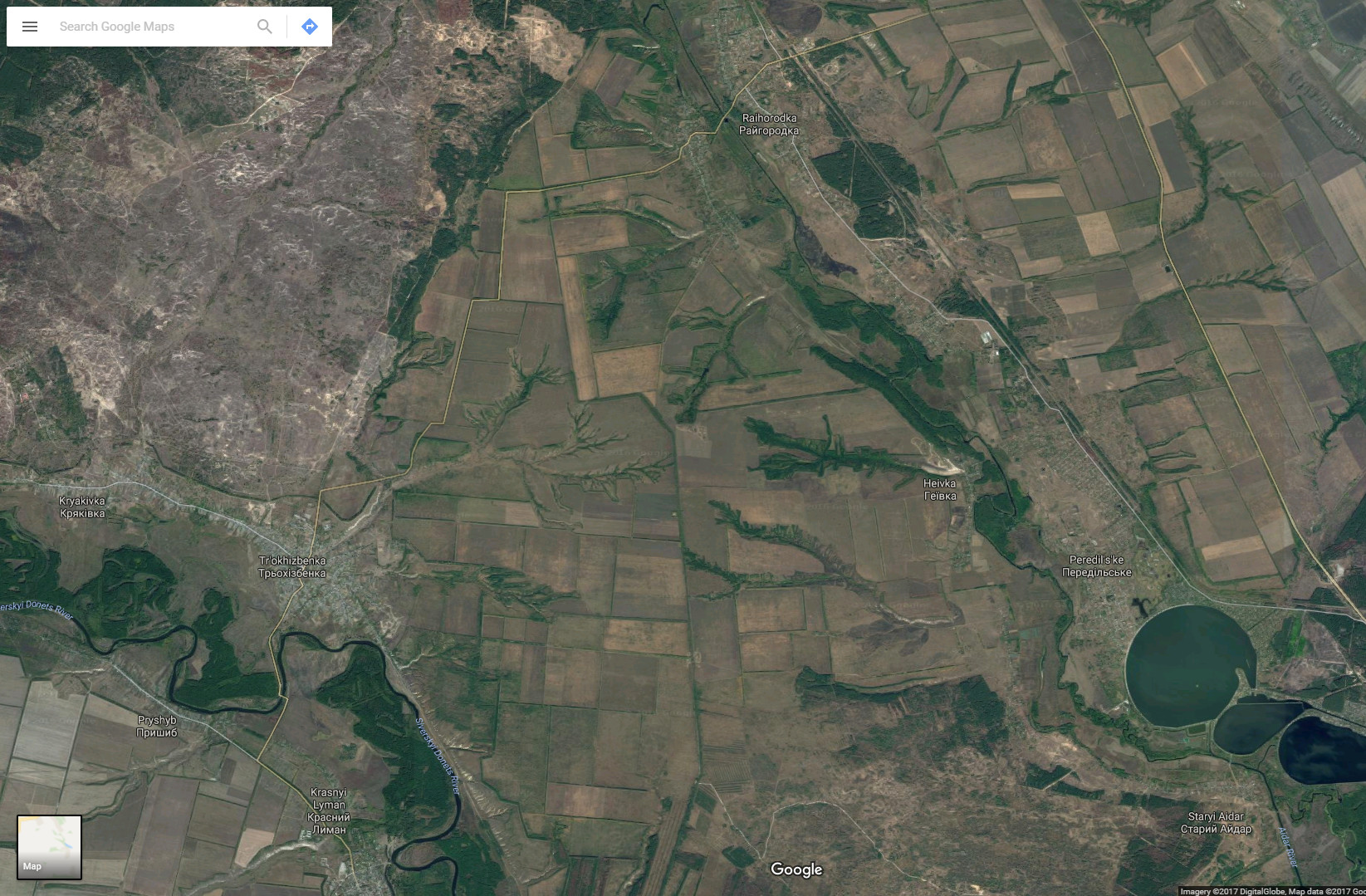
According to the report, the Orlan-10 drone, number 10253, controlled by Senior Lieutenant Yevgeny Yakeyev and Yefreytor Rodion Savvovich Urekyanu (two of the soldiers confirmed as active Russian military by UCA and InformNapalm) took off from occupied Lugansk city, flying over Stanitsa Luganskaya, Schastye and Tryokhizbenka, before returning to its launch site.
The mission aim is described as follows:
“Conduct aerial reconnaissance in the designated areas. Correcting artillery fire.”
The report states that at 16:24 that day, two armoured vehicles and six other vehicles were spotted Stanitsa Luganskaya.
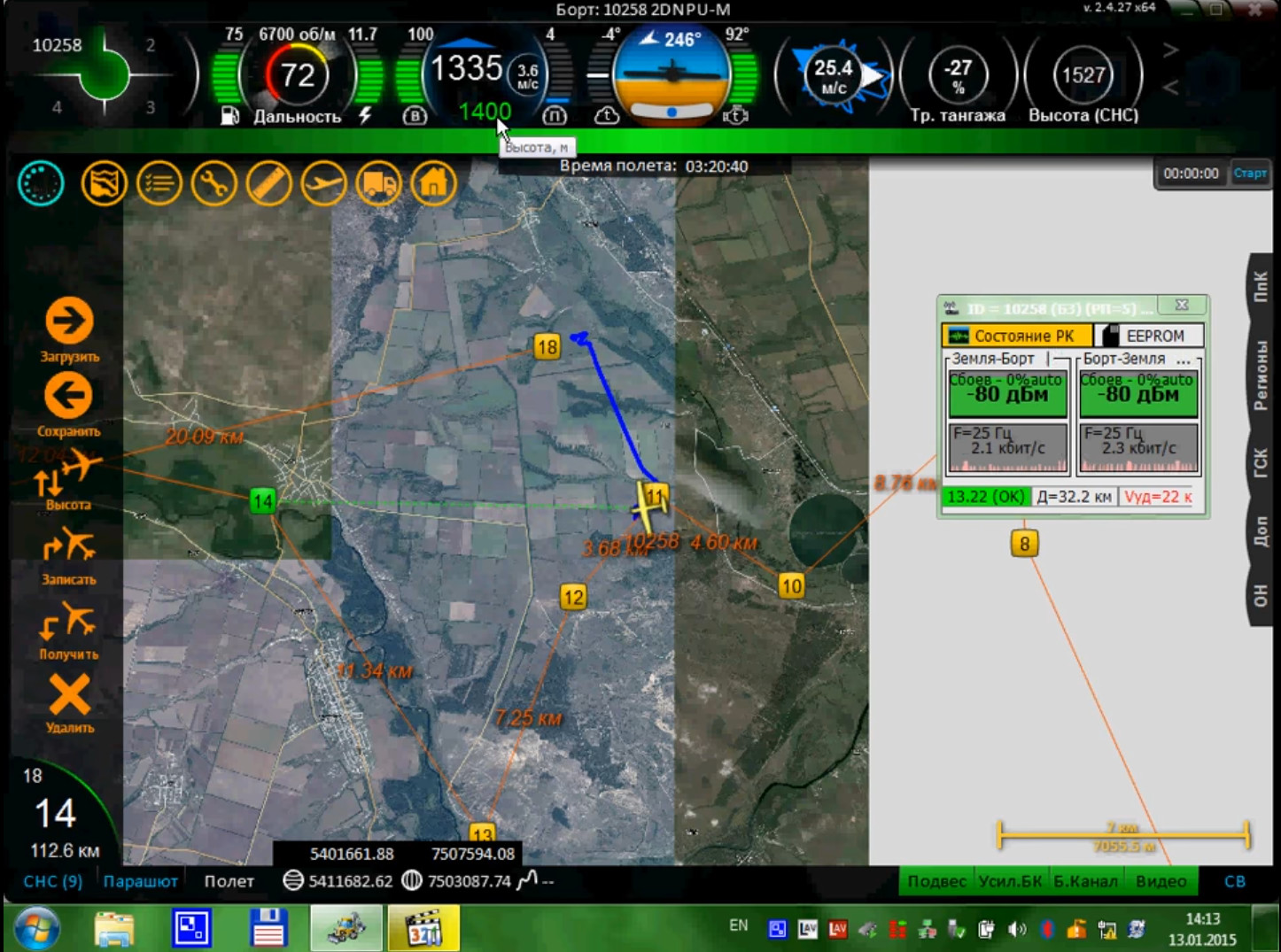
Even more amazingly, a video has been released by InformNapalm, apparently filmed by a Russian drone operator, recording their computer screen while directing an Orlan-10 (number 10258) over Ukrainian-controlled territory just west of Schastye on January 13, 2015:
The software interface seen in the video matches that seen in photographs from this blog, taken in December, 2014, during a tour of the Russian Ministry of Defense’s 924th UAV training center in Kolomna, in the Moscow region:

Five Downed Russian Drones in Ukraine
Open source tracking of the production, deployment, and downing of five Russian Forpost UAVs in the Donbas Recently, independent Ukrainian blogger Askai707 found new photographs of a crashed Forpost unmanned aerial vehicle (UAV, or drone) in the village of Novopetrivs'ke in the Donetsk Oblast, from August 2014.
The presence of these drones in Ukraine is one of the most straightforwards pieces of evidence of Russia’s direct military participation in the Ukraine war.
— Pierre Vaux